The NIST 800-61 revision 2 standard provides guidelines for incident handling, especially for analyzing incident-related data, and determining the appropriate response to each incident. The guidelines can be followed independently of particular hardware platforms, operating systems, protocols, or applications.
Organizations that need to implement the NIST Incident Response Life Cycle, must first establish a computer security incident response capability (CSIRC). NIST recommends creating policies, plans, and procedures for establishing and maintaining a CSIRC.
The NIST 800-62 revision 2 defines four steps in the incident response process life cycle.
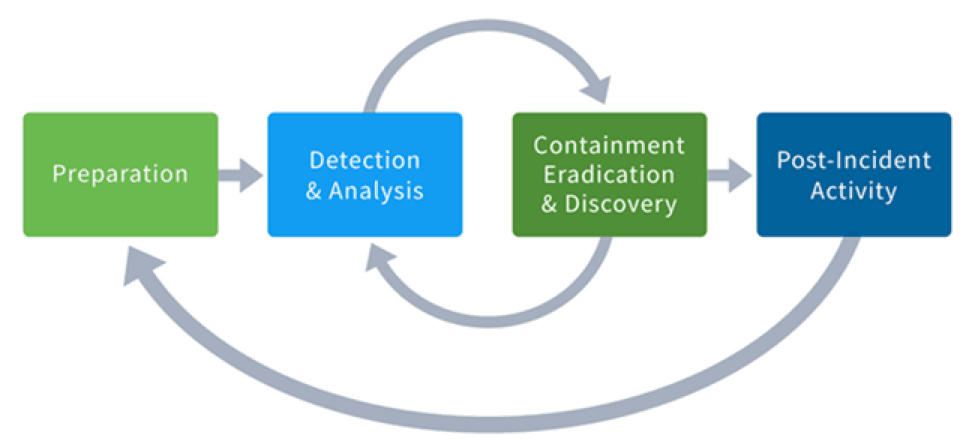
Preparation: At this phase, the CSIRT is created and trained on how to respond to an incident. Tools, assets, and resources that will be needed by the team to investigate incidents are acquired and deployed. The CSIRT may have a jump kit prepared. CSIRT members should continually develop knowledge of emerging threats.
Detection and Analysis: The CSIRT must react quickly to validate and analyze incidents through continuous monitoring.
Incident Detection includes collecting data from sources, security tools, publicly available information, and people inside and outside the organization, and identifying precursors (signs that an incident may happen in the future) and indicators (data showing that an attack has happened or is happening).
Incident Analysis include identifying activities for the affected systems, correlating related events, and seeing if and how they deviate from normal behavior. Sometimes, Incident analysis is difficult because not all of the indicators are accurate.
Containment, Eradication, and Recovery: The CSIRT implements procedures to contain the threat, eradicate its impact on organizational assets, and use backups to restore data. Sometimes, this phase may cycle back to detection and analysis to gather more information or to expand the scope of the investigation.
Once the threat has been detected it must be contained to determine what to do about it. After threat eradication, system restoration, and recovery, steps needs to be taken to ensure that the same assets are not attacked again.
Post-Incident Activities: After the organization has recovered from the effects of the attack, it is important to take a step back and meet to discuss the events that took place and the action taken while handling the incident. This will provide an avenue to learn what was done right, what was done wrong, and what should be improved upon.
You should ask, investigate and document the answers to the following questions:
- What happened, and at what times?
- How well did the incident response team deal with the incident? Were processes followed, and were they sufficient?
- What information was needed sooner?
- Were any wrong actions taken that caused damage or inhibited recovery?
- What could staff do differently next time if the same incident occurred?
- Could staff have shared information better with other organizations or other departments?
- Have we learned ways to prevent similar incidents in the future?
- Have we discovered new precursors or indicators of similar incidents to watch for in the future?
- What additional tools or resources are needed to help prevent or mitigate similar incidents?
The CSIRT then documents how the incident was handled, recommends changes for a future response, and specifies how to avoid a reoccurrence.